Enforce Zero-Trust with Identity Security
HaloTrust integrates device posture with user identity to provide granular, dynamic access control, protecting your applications, networks, and data.
Identity-Aware Endpoint Management
HaloFort unifies endpoints, fortifies Zero Trust with identity integration, and streamline patch management with automated compliance.
Why HaloTrust?
40%
Stronger Access Control
Only MFA-verified, UEM-enrolled devices gain access, blocking unmanaged endpoints and reducing the likelihood of multimillion-dollar data breaches
40%
Stronger Access Control
Only MFA-verified, UEM-enrolled devices gain access, blocking unmanaged endpoints and reducing the likelihood of multimillion-dollar data breaches
40%
Stronger Access Control
Only MFA-verified, UEM-enrolled devices gain access, blocking unmanaged endpoints and reducing the likelihood of multimillion-dollar data breaches
40%
Stronger Access Control
Only MFA-verified, UEM-enrolled devices gain access, blocking unmanaged endpoints and reducing the likelihood of multimillion-dollar data breaches
40%
Prevent Threats, Protect Business
Automated patching, antivirus, and CVE remediation shrink exploit windows and cut manual work, lowering IT operations costs by 30–40% through automation.
40%
Prevent Threats, Protect Business
Automated patching, antivirus, and CVE remediation shrink exploit windows and cut manual work, lowering IT operations costs by 30–40% through automation.
40%
Prevent Threats, Protect Business
Automated patching, antivirus, and CVE remediation shrink exploit windows and cut manual work, lowering IT operations costs by 30–40% through automation.
40%
Prevent Threats, Protect Business
Automated patching, antivirus, and CVE remediation shrink exploit windows and cut manual work, lowering IT operations costs by 30–40% through automation.
50%
Secure Productivity Anywhere
Conditional access, adaptive MFA, and just-in-time privileges keep users productive without compromising security, while reducing password-related IT helpdesk tickets by up to 50%.
50%
Secure Productivity Anywhere
Conditional access, adaptive MFA, and just-in-time privileges keep users productive without compromising security, while reducing password-related IT helpdesk tickets by up to 50%.
50%
Secure Productivity Anywhere
Conditional access, adaptive MFA, and just-in-time privileges keep users productive without compromising security, while reducing password-related IT helpdesk tickets by up to 50%.
50%
Secure Productivity Anywhere
Conditional access, adaptive MFA, and just-in-time privileges keep users productive without compromising security, while reducing password-related IT helpdesk tickets by up to 50%.
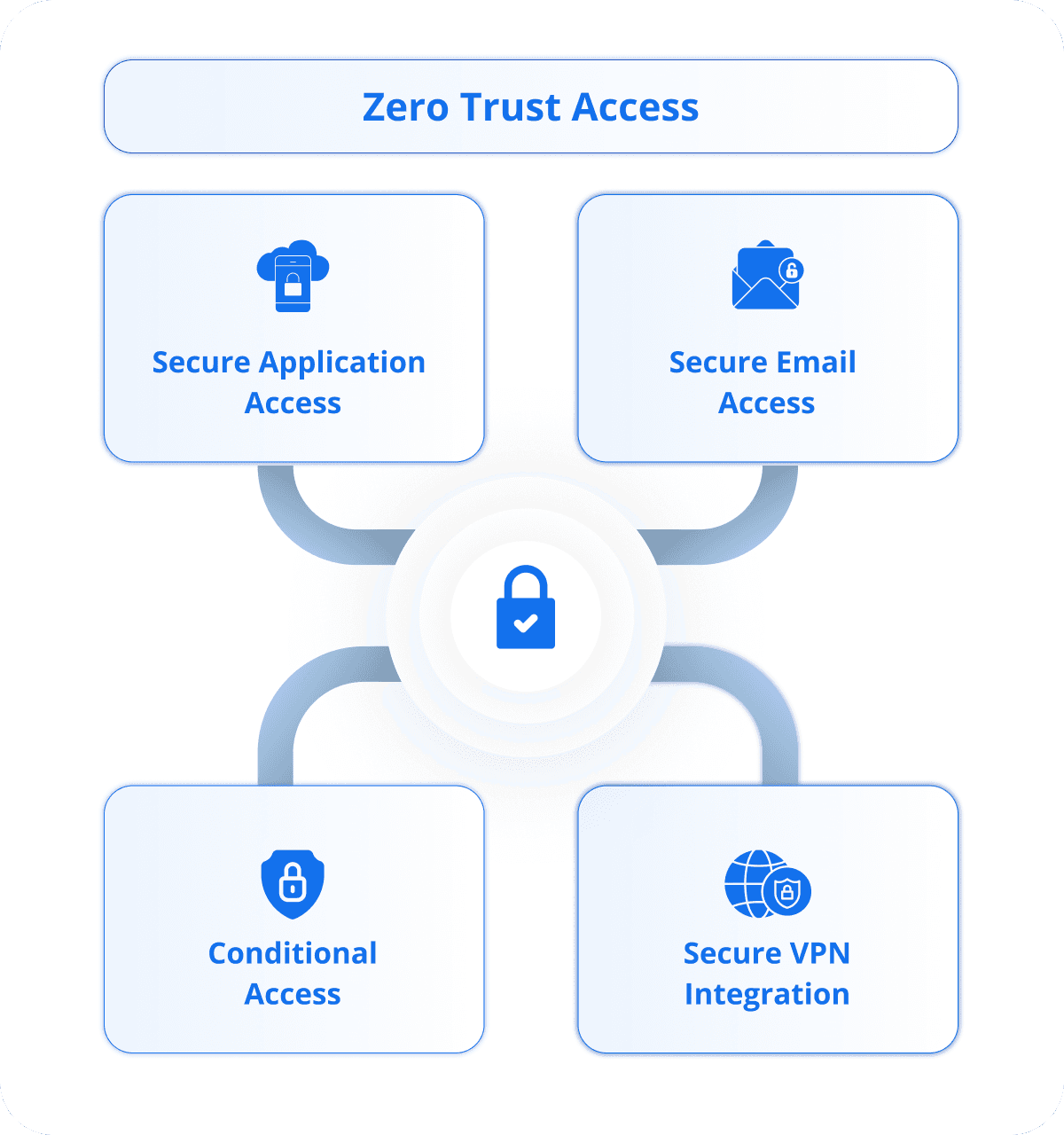
Zero Trust Access
Securing access to applications and networks using Zero Trust principles, conditional access and VPN ensuring verification at every step.
Secure Application Access
Secures access to web, desktop, cloud, and on-premise applications by enforcing strict verification protocols.
Secure Application Access
Secures access to web, desktop, cloud, and on-premise applications by enforcing strict verification protocols.
Secure Application Access
Secures access to web, desktop, cloud, and on-premise applications by enforcing strict verification protocols.
Secure Application Access
Secures access to web, desktop, cloud, and on-premise applications by enforcing strict verification protocols.
Secure Email Access
Ensures protected access to email services by verifying user identity, device posture, and context before allowing connections.
Secure Email Access
Ensures protected access to email services by verifying user identity, device posture, and context before allowing connections.
Secure Email Access
Ensures protected access to email services by verifying user identity, device posture, and context before allowing connections.
Secure Email Access
Ensures protected access to email services by verifying user identity, device posture, and context before allowing connections.
Conditional Access
Leverages device compliance status to dynamically grant or deny access to corporate resources like Microsoft 365 and Google Workspace.
Conditional Access
Leverages device compliance status to dynamically grant or deny access to corporate resources like Microsoft 365 and Google Workspace.
Conditional Access
Leverages device compliance status to dynamically grant or deny access to corporate resources like Microsoft 365 and Google Workspace.
Conditional Access
Leverages device compliance status to dynamically grant or deny access to corporate resources like Microsoft 365 and Google Workspace.
Secure VPN Integration
Allows centralized setup of VPN profiles and policies through HaloUEM, including per-app or full-device VPN.
Secure VPN Integration
Allows centralized setup of VPN profiles and policies through HaloUEM, including per-app or full-device VPN.
Secure VPN Integration
Allows centralized setup of VPN profiles and policies through HaloUEM, including per-app or full-device VPN.
Secure VPN Integration
Allows centralized setup of VPN profiles and policies through HaloUEM, including per-app or full-device VPN.



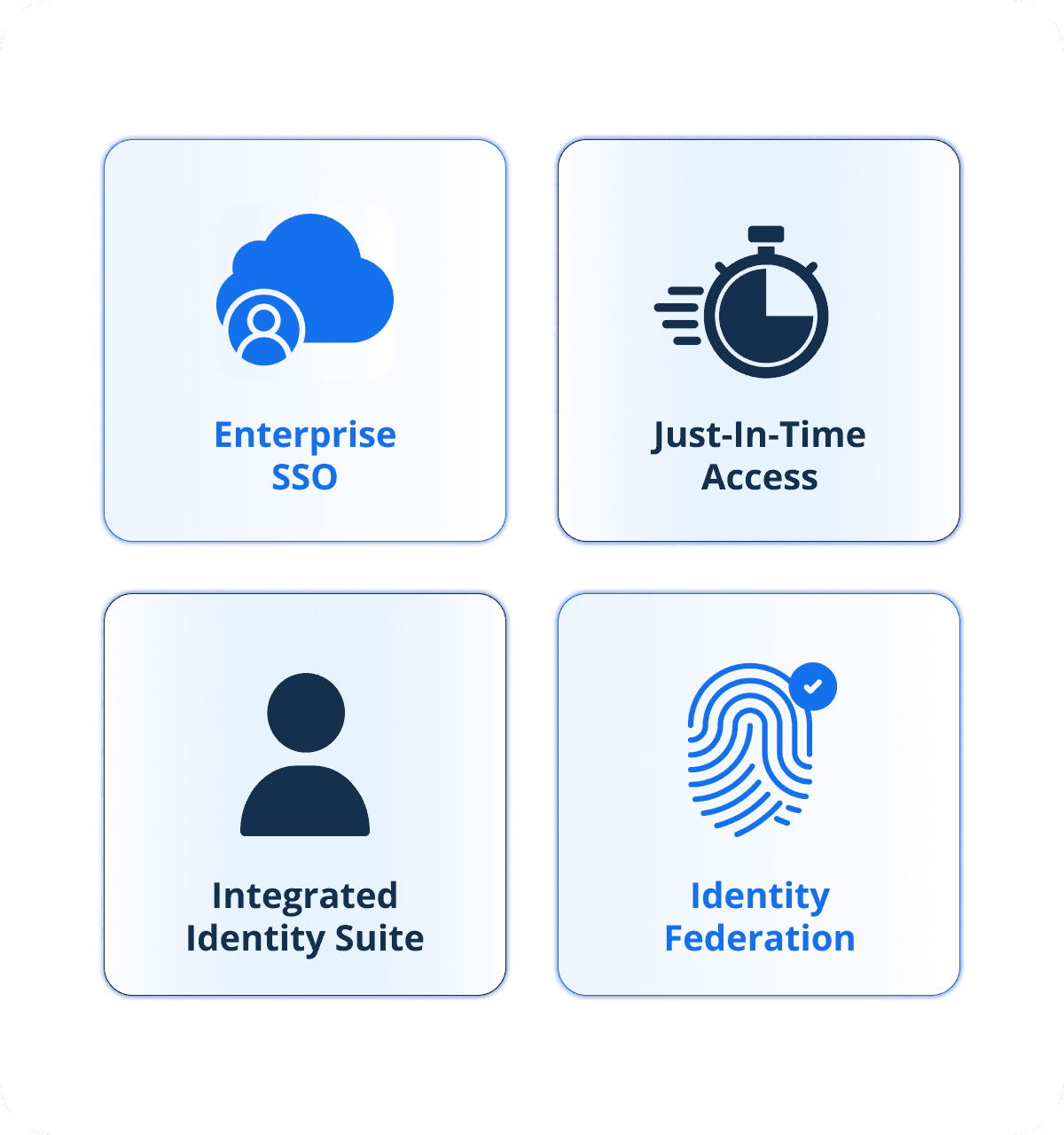



Identity and Access Management
Manage user identities, access rights, and privileges to minimize risks from unauthorized actions.
Enterprise SSO
Enterprise Single Sign-On for admin console and end-user portal, streamlining secure authentication.
Enterprise SSO
Enterprise Single Sign-On for admin console and end-user portal, streamlining secure authentication.
Enterprise SSO
Enterprise Single Sign-On for admin console and end-user portal, streamlining secure authentication.
Enterprise SSO
Enterprise Single Sign-On for admin console and end-user portal, streamlining secure authentication.
Just-In-Time Access
Eliminates standing privileges and grants just-in-time administrative rights via Endpoint Privilege Management (EPM).
Just-In-Time Access
Eliminates standing privileges and grants just-in-time administrative rights via Endpoint Privilege Management (EPM).
Just-In-Time Access
Eliminates standing privileges and grants just-in-time administrative rights via Endpoint Privilege Management (EPM).
Just-In-Time Access
Eliminates standing privileges and grants just-in-time administrative rights via Endpoint Privilege Management (EPM).
Integrated Identity Suite
Offers UEM-Driven Zero Trust Access, Conditional SSO, and Endpoint Device Authentication (Keycard) through HaloIDP.
Integrated Identity Suite
Offers UEM-Driven Zero Trust Access, Conditional SSO, and Endpoint Device Authentication (Keycard) through HaloIDP.
Integrated Identity Suite
Offers UEM-Driven Zero Trust Access, Conditional SSO, and Endpoint Device Authentication (Keycard) through HaloIDP.
Integrated Identity Suite
Offers UEM-Driven Zero Trust Access, Conditional SSO, and Endpoint Device Authentication (Keycard) through HaloIDP.
Identity Federation
Supports federation with external identity providers like Google Workspace, Entra ID, Okta, and AD for seamless integration.
Identity Federation
Supports federation with external identity providers like Google Workspace, Entra ID, Okta, and AD for seamless integration.
Identity Federation
Supports federation with external identity providers like Google Workspace, Entra ID, Okta, and AD for seamless integration.
Identity Federation
Supports federation with external identity providers like Google Workspace, Entra ID, Okta, and AD for seamless integration.
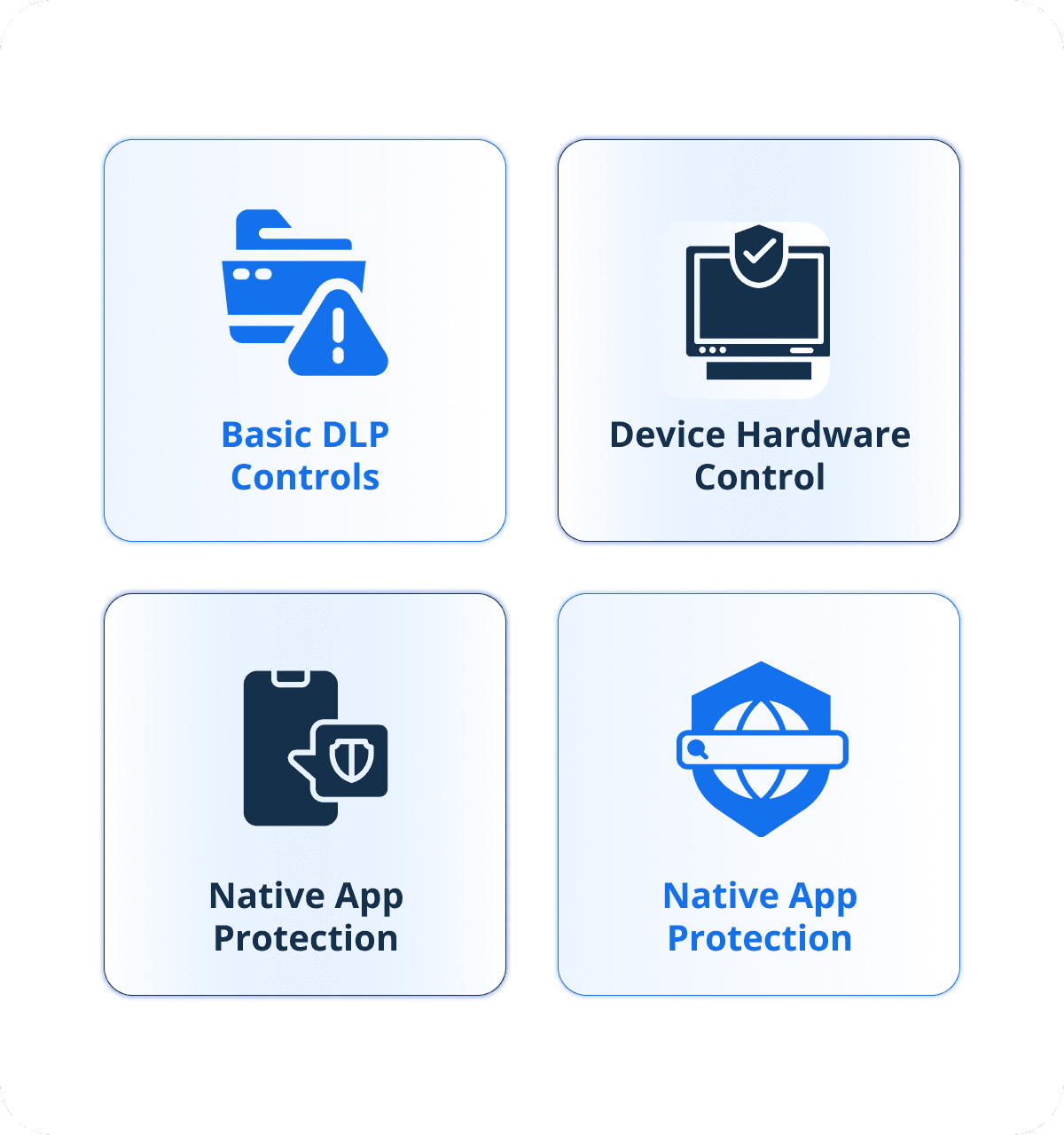
Data and Device Protection
Safeguard your endpoints for data integrity and device security, preventing leaks and unauthorized hardware usage.
Basic DLP Controls
Provides basic Data Loss Prevention (DLP) features like copy/paste and screenshot blocking, plus encryption management (BitLocker, FileVault).
Basic DLP Controls
Provides basic Data Loss Prevention (DLP) features like copy/paste and screenshot blocking, plus encryption management (BitLocker, FileVault).
Basic DLP Controls
Provides basic Data Loss Prevention (DLP) features like copy/paste and screenshot blocking, plus encryption management (BitLocker, FileVault).
Basic DLP Controls
Provides basic Data Loss Prevention (DLP) features like copy/paste and screenshot blocking, plus encryption management (BitLocker, FileVault).
Device Hardware Control
Enables hardware restrictions to disable features such as cameras, USB ports, and Bluetooth for enhanced security.
Device Hardware Control
Enables hardware restrictions to disable features such as cameras, USB ports, and Bluetooth for enhanced security.
Device Hardware Control
Enables hardware restrictions to disable features such as cameras, USB ports, and Bluetooth for enhanced security.
Device Hardware Control
Enables hardware restrictions to disable features such as cameras, USB ports, and Bluetooth for enhanced security.
Native App Protection
Delivers application protection for organisation apps across Android, iOS, Windows, and macOS with conditional access.
Native App Protection
Delivers application protection for organisation apps across Android, iOS, Windows, and macOS with conditional access.
Native App Protection
Delivers application protection for organisation apps across Android, iOS, Windows, and macOS with conditional access.
Native App Protection
Delivers application protection for organisation apps across Android, iOS, Windows, and macOS with conditional access.
Web Browsing Protection
Offers category-based web browsing protection for major browsers (Chrome, Safari, Firefox, Opera).
Web Browsing Protection
Offers category-based web browsing protection for major browsers (Chrome, Safari, Firefox, Opera).
Web Browsing Protection
Offers category-based web browsing protection for major browsers (Chrome, Safari, Firefox, Opera).
Web Browsing Protection
Offers category-based web browsing protection for major browsers (Chrome, Safari, Firefox, Opera).



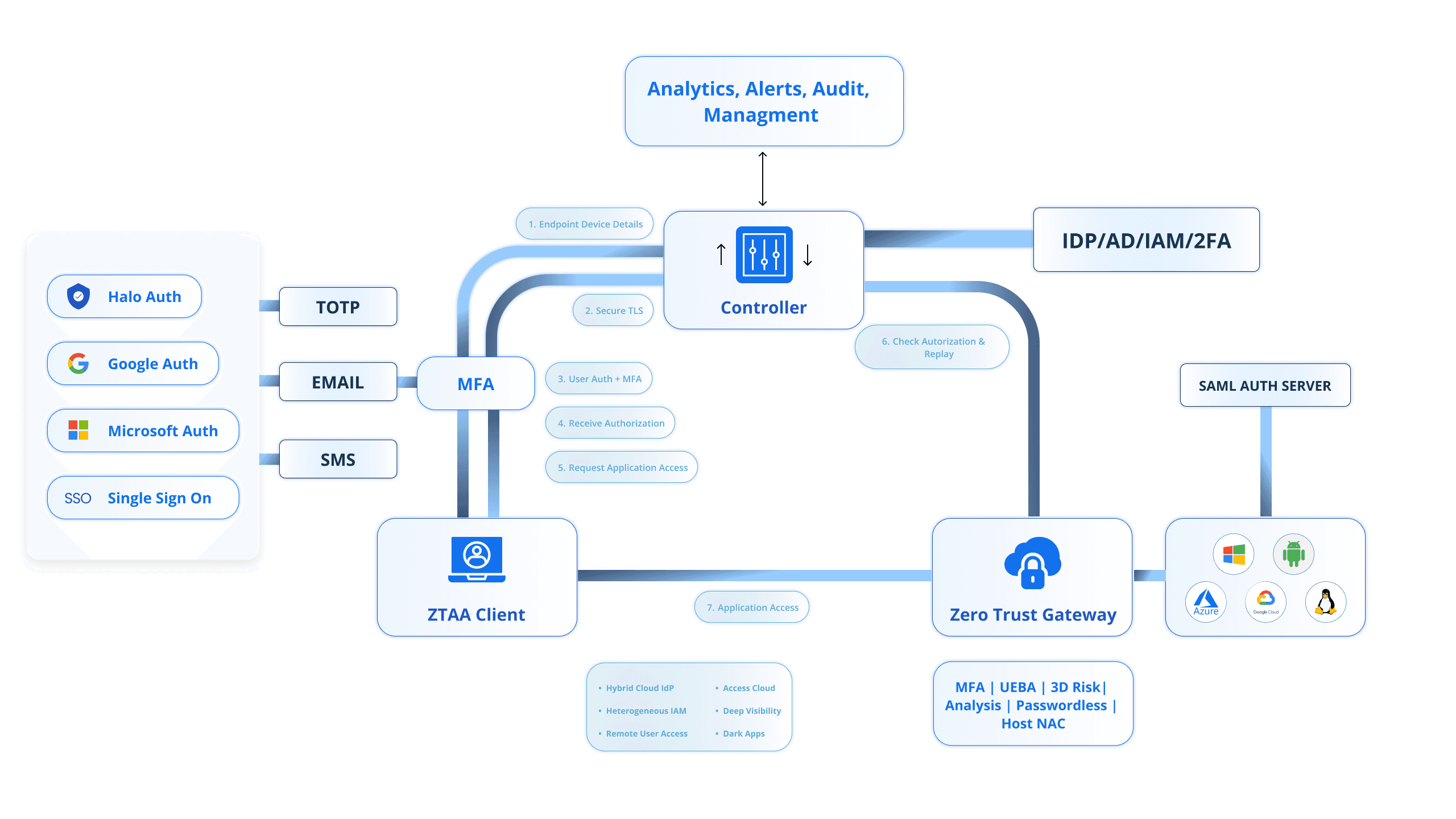
How HaloTrust Works?
HaloTrust implements Zero Trust and IDP security by real-time verification of user identity and device status for access control, including data protection and privileges.
#HaloTrust
#ZeroTrust
#IdentityDriven
#ConditionalAccess
#MFA



Additional Features
HaloTrust provides additional specialised features that support overall security, compliance, and threat response.
Automated Monitoring
Automatically monitors and remediates device configurations to ensure continuous compliance with security baselines.
Automated Monitoring
Automatically monitors and remediates device configurations to ensure continuous compliance with security baselines.
Automated Monitoring
Automatically monitors and remediates device configurations to ensure continuous compliance with security baselines.
Automated Monitoring
Automatically monitors and remediates device configurations to ensure continuous compliance with security baselines.
HaloConnect VPN
HaloFort's built-in VPN for secure per-app tunneling and zero-trust access, safeguarding data across all devices without full traffic routing.
HaloConnect VPN
HaloFort's built-in VPN for secure per-app tunneling and zero-trust access, safeguarding data across all devices without full traffic routing.
HaloConnect VPN
HaloFort's built-in VPN for secure per-app tunneling and zero-trust access, safeguarding data across all devices without full traffic routing.
HaloConnect VPN
HaloFort's built-in VPN for secure per-app tunneling and zero-trust access, safeguarding data across all devices without full traffic routing.
Contextual Fencing
Implements geo-fencing, time-fencing, network-fencing, and Wi-Fi-fencing for dynamic, location-based security policies.
Contextual Fencing
Implements geo-fencing, time-fencing, network-fencing, and Wi-Fi-fencing for dynamic, location-based security policies.
Contextual Fencing
Implements geo-fencing, time-fencing, network-fencing, and Wi-Fi-fencing for dynamic, location-based security policies.
Contextual Fencing
Implements geo-fencing, time-fencing, network-fencing, and Wi-Fi-fencing for dynamic, location-based security policies.
Adaptive Access Policies
Delivers real-time protection against mobile-specific threats like malware, phishing, and network exploits.
Adaptive Access Policies
Delivers real-time protection against mobile-specific threats like malware, phishing, and network exploits.
Adaptive Access Policies
Delivers real-time protection against mobile-specific threats like malware, phishing, and network exploits.
Adaptive Access Policies
Delivers real-time protection against mobile-specific threats like malware, phishing, and network exploits.

Experience HaloFort Today
Are you ready to unify your endpoint IT and security?

Experience HaloFort Today
Are you ready to unify your endpoint IT and security?

Experience HaloFort Today
Are you ready to unify your endpoint IT and security?

Experience HaloFort Today
Are you ready to unify your endpoint IT and security?





